WARNING
This procedure requires an outage for production. Please plan accordingly
To migrate to the TLS-enabled components, all the existing deployments for Redis, Mongo, PostgreSQL, and ActiveMQ
Backup
Before proceeding with the migration to TLS-enabled release, please take a backup of all the applications using the guide available at Mongo, PostgreSQL Backup/Restore Procedure for EF-CX on Kubernetes (manual procedure)
Once the backup has been taken, follow this guide to enable TLS for StatefulSets artifacts.
Change your working directory
cd ~/cim-solution/kubernetes
Upgrade Mongo to enable TLS/Auth
Uninstall the Mongo Helm chart
helm -n ef-external delete mongo
Once the chart is removed, install the chart from the appropriate release with TLS and Auth enabled
helm upgrade --install --namespace ef-external --values=external/bitnami/mongo/value.yaml mongo external/bitnami/mongo
Once the Mongo deployment is ready, restore the previous backup mentioned in this guide.
Upgrade Redis to enable TLS/Auth
Uninstall the existing Redis deployment
helm -n ef-external delete redis
Deploy the Redis chart from the latest release with TLS and Auth enabled
helm upgrade --install --namespace ef-external --values=external/bitnami/redis/values.yaml redis external/bitnami/redis
Upgrade PostgreSQL to enable TLS/Auth
Uninstall the existing PostgreSQL helm chart
helm -n ef-external delete ef-postgresql
Upgrade the Postgresql using the latest TLS/Auth-enabled release
helm upgrade --install --namespace ef-external --values=external/bitnami/postgresql/values.yaml ef-postgreql external/bitnami/postgresql
Once the PostgreSQL deployment is ready, restore the backup.
Verify
After enabling TLS, we can verify it by following these steps:-
-
list all pods in namespace ef-external
kubectl get pods -n ef-external
the output will be similar to this

-
Identify the pod you want to verify and run the following command after updating the pod name.
kubectl describe pod <pod-name> -n ef-external
the output will be as follows, scroll to Environment to get the tlsCertificateKeyFile and tlsCAFile directories as mentioned below:-
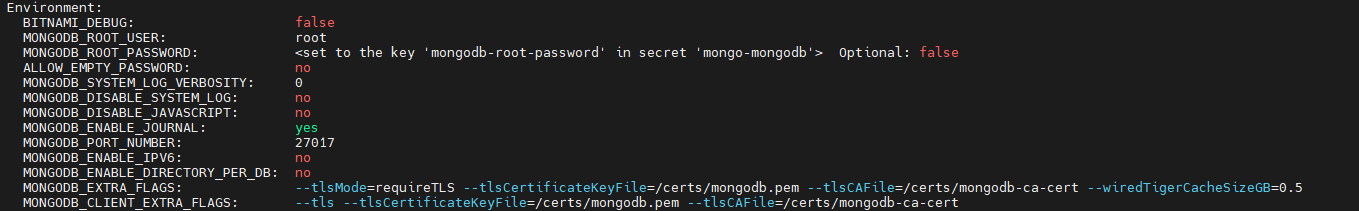
3. Now exec into the client pod using the following command:-
kubectl run --namespace ef-external mongo-mongodb-client --rm --tty -i --restart='Never' --env="MONGODB_ROOT_PASSWORD=$MONGODB_ROOT_PASSWORD" --image docker.io/bitnami/mongodb:6.0.2-debian-11-r1 --command -- bash
-
now run the following connection string to connect to the pod:-
mongosh admin --host "mongo-mongodb" --authenticationDatabase admin -u root -p $MONGODB_ROOT_PASSWORD --tls --tlsAllowInvalidHostnames --tlsAllowInvalidCertificates --tlsCertificateKeyFile <tlsCertificateKeyFile > --tlsCAFile <tlsCAFile>
-
Once the connection is established, the verification is completed.