This document covers the setup for importing the pre-configured realm in Keycloak.
-
For release HC 4.1 or backward download the realm-export.json file and place it in any directory of your choice.
-
For release CX-4.1 and onwards download the realm-export-4.1-onwards.json file and place it in any directory of your choice.
-
For release CX-4.3 and onwards download the realm-export-4.3.json file and place it in any directory of your choice.
-
For release CX-4.5.1 download the 4.5.1-realm.json file and place it in any directory of your choice.
-
For release CX-4.5.2 and onwards download the 4.5.2-realm.json file and place it in any directory of your choice.
-
For release CX-4.7 and onwards, download the 4.7-realm.json file and place it in any directory of your choice. This file doesn't contain permissions for Campaigns and Surveys, they should be imported separately.
-
If you've not imported the realm and its users using the above realm file & upgrade script, then you can create a realm, client, roles, and an admin user following these steps:
Login to the KeyCloak Administration console by browsing your Keycloak server URL: https://<server-fqdn>/auth.
-
Log in to the administration console using the password set in environment variables (KEYCLOAK_USERNAME and KEYCLOAK_PASSWORD). Default username is admin and password is admin.
-
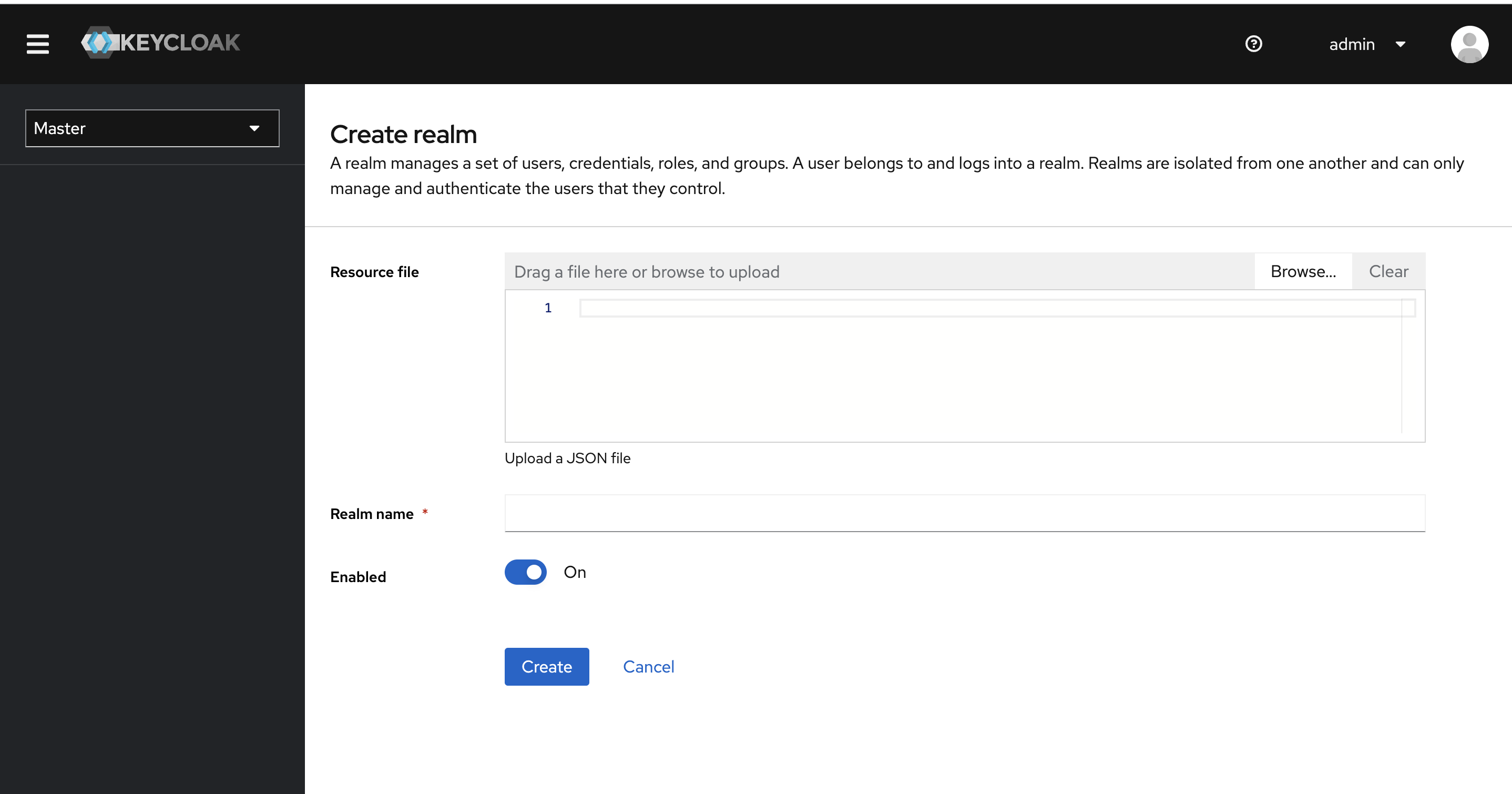
Bring the cursor to the master realm and click on Add realm button.
-
Click on the Select file button and select the realm-export.json file downloaded in step 1 and press Create.

-
This will create the expertflow realm with all required configurations.
-
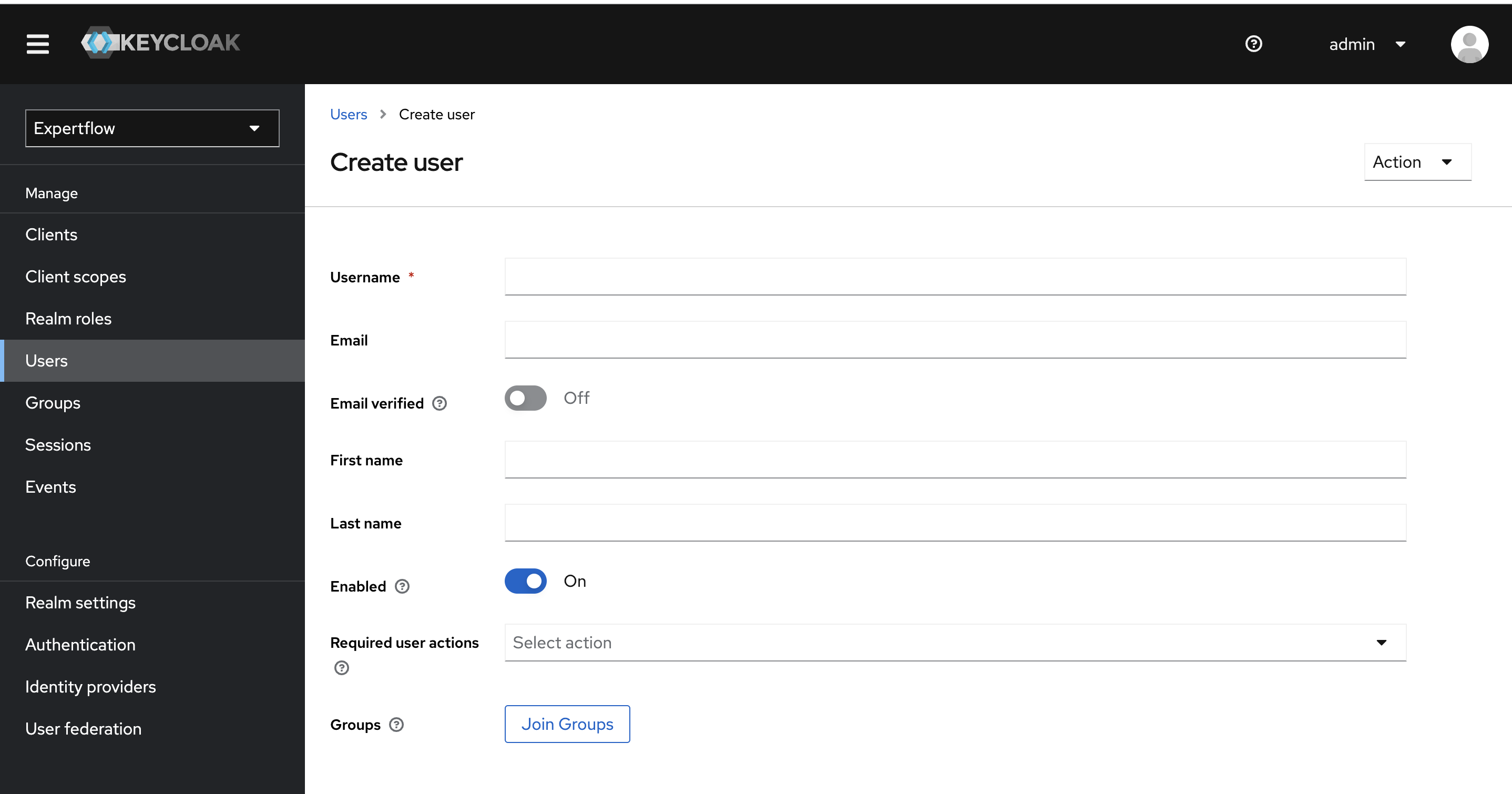
Once realm is imported, we need to create create the users in our example agent/supervisor and admin. To create a user click on Users from the left nav bar.
-
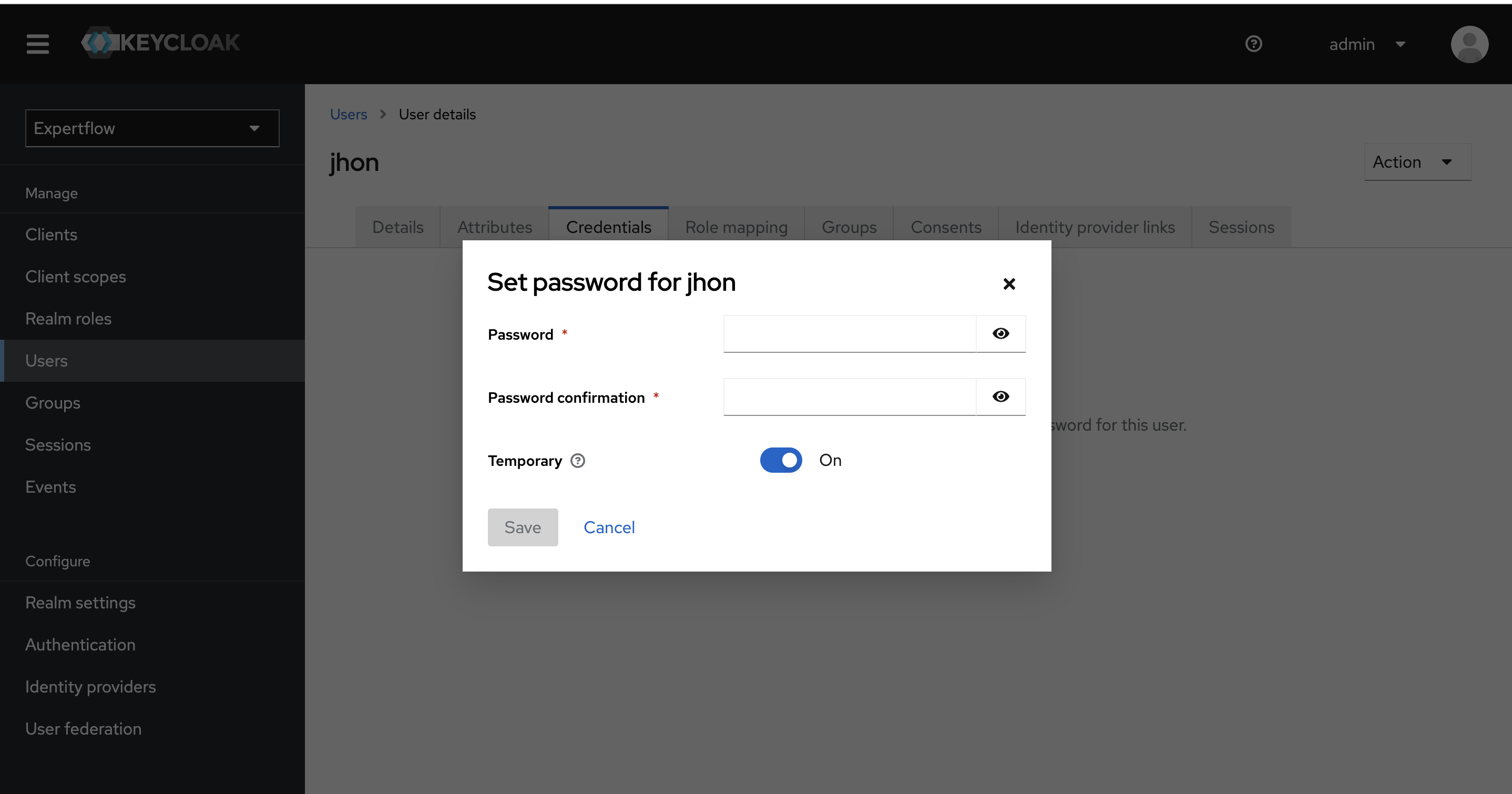
Once the user is created, we can see additional fields at the top (Details, Attributes, Credentials). Now select the Credentials tab and click on Set Password button. Type the password of your choice, also turn Temporary to off
-
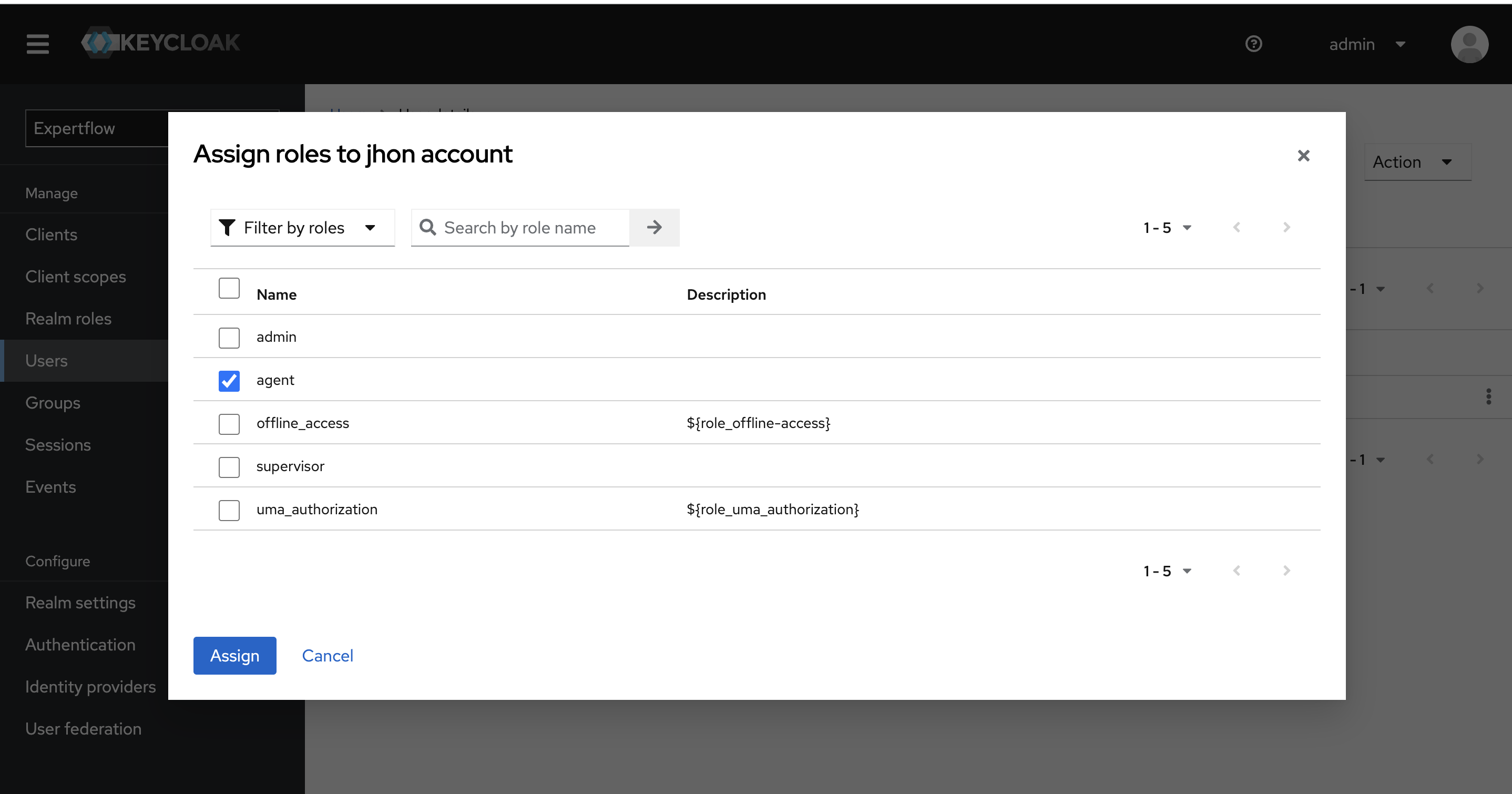
To assign the roles to the user, click on the Role Mappings tab on top and click on Assign Role Button. In the pop-up window, we can see admin, agent and supervisor roles, for agent user assign agent role and for supervisor user assign supervisor role. Assign offline_access and uma_authorization roles as well.
agent role must be assigned to the Agent user if agents_permission group is assigned. supervisor role must be assigned to the Supervisor user if agents_permission and senior_agents_permission groups are assigned.
4.5.1 Onwards: Supervisor and Senior Agent must be assigned senior_agents_permission group. senior_agents_permission became superset of agents_permission group (If we assign senior_agents_permission then all the permissions of agents_permission will be automatically assigned to agent/supervisor).
-
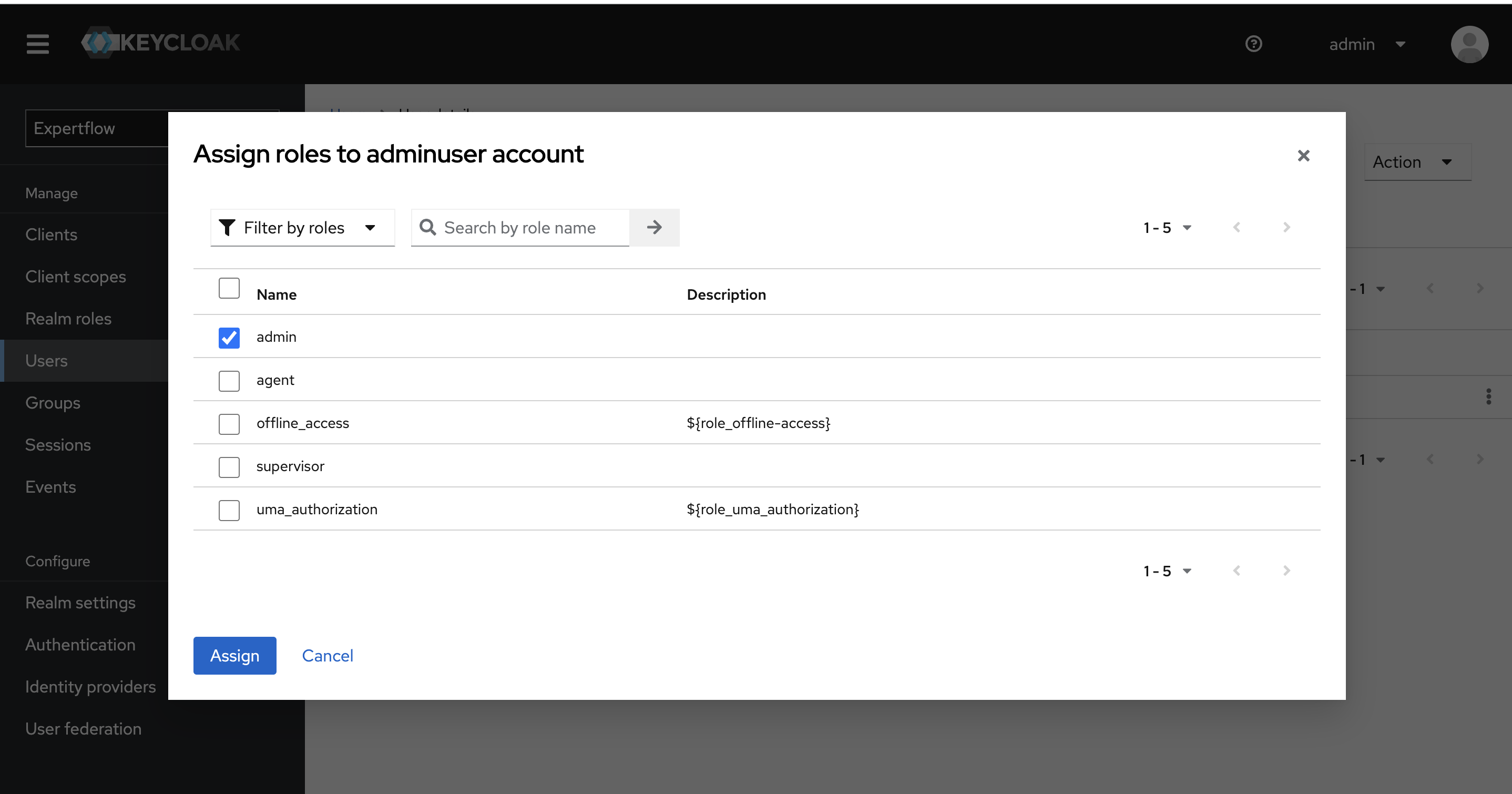
For admin-user first select the admin, offline_access and uma_authorization from Roles and click on Assign button. This will assign realm-roles to the admin user in Keycloak.
-
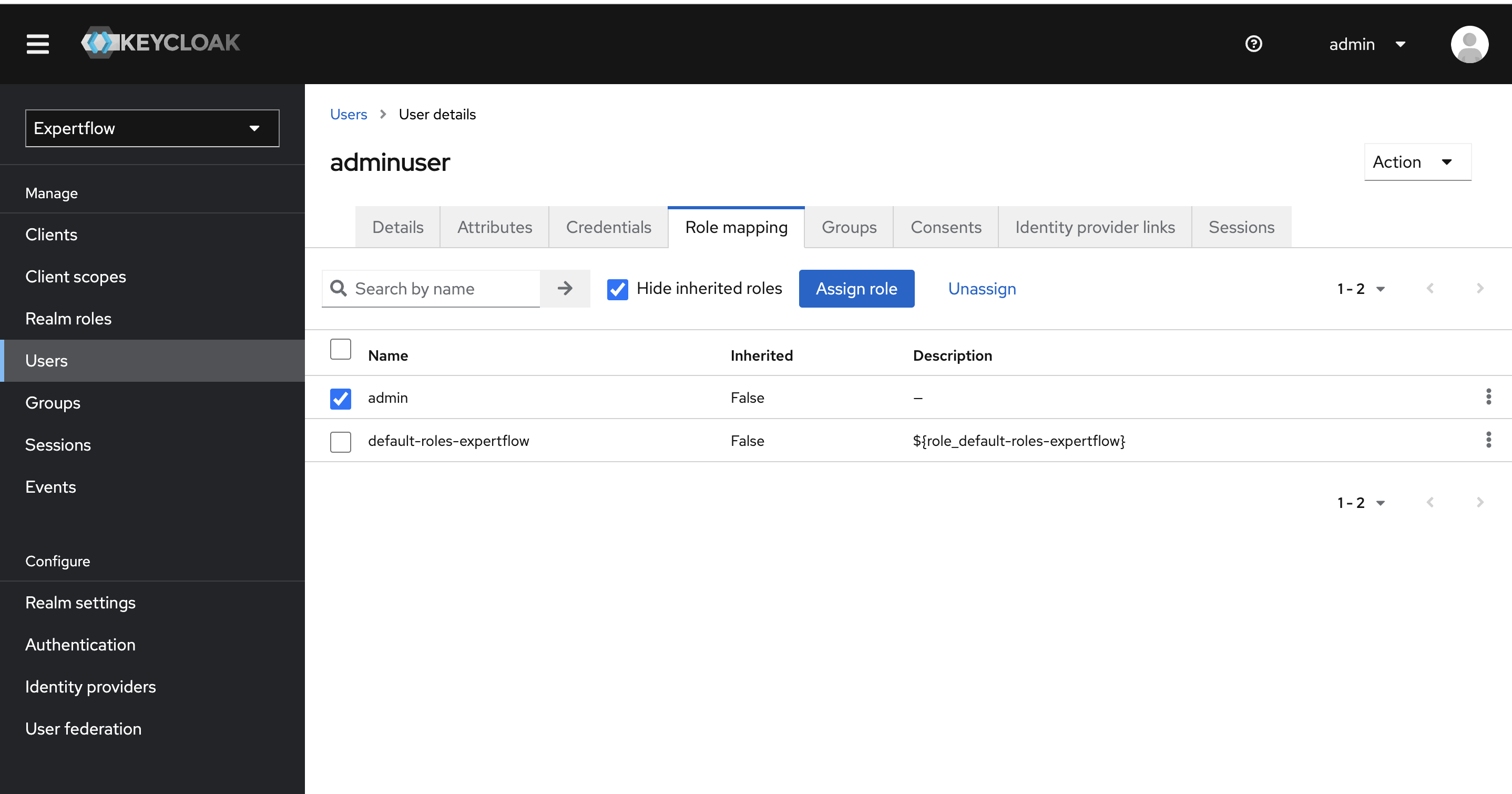
Select the admin user from users list and click on Assign Role Button.
-
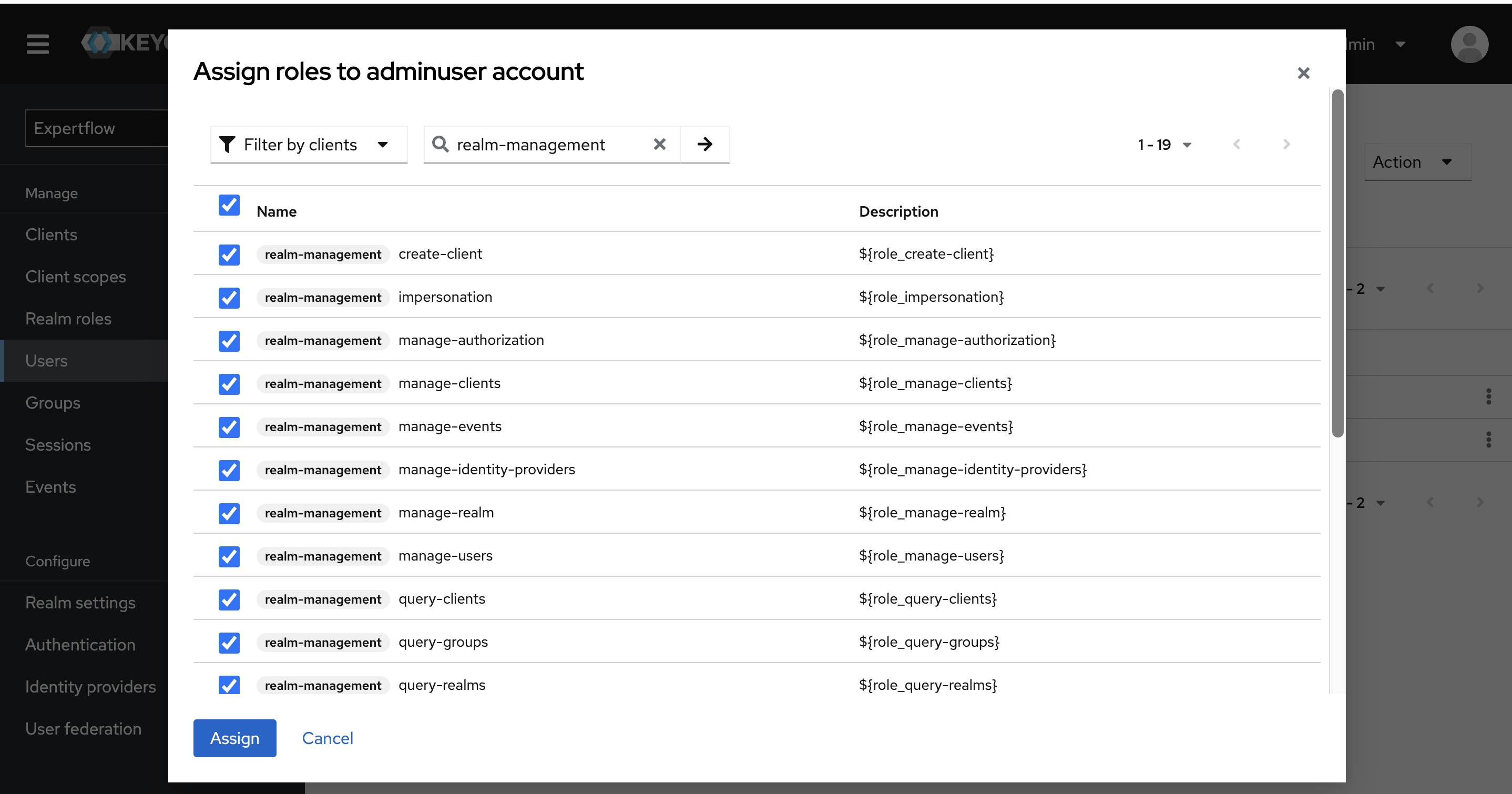
Select the Filter by clients filter and search all realm-management roles. Select all realm-management roles and click on Assign button.
Assign all 23 roles to admin user i.e 19 realm-management roles, admin role, default-roles-<Realm-Name> role, offline_access and uma_authorization roles.
-
A user shouldn’t have more than one custom CX roles assigned to it.
-
If user has an admin role then it shouldn’t have an agent/supervisor or any other role assigned to it. Same for all other roles, one users should only have one CX role assigned to it apart from uma_authorization, offline_access and default-roles-expertflow.
-
-
Follow User's Teams Configuration guide to create and assign users to the team.
-
Team assignment is mandatory for agent and supervisor roles only. Users with other roles i.e (i.e admin, routing-manager, quality-manager etc) are not required to be assigned to a team. Make sure only users with agent or supervisor roles are part of team. Remove all user from teams with neither of role assigned to them, its mandatory.