This document describes the process of whisper coaching gadget deployment.
Gadget Deployment Planning
The whisper coaching gadget is a combination of the 2 components.
|
Solution Components |
Description |
|---|---|
|
API Service |
This is a Java-based rest service that requires tomcat to run. |
|
Gadget Specifications files for Finesse |
Finesse gadget specifications files which render frontend inside Cisco Finesse. |
Prerequisites
Following are the mandatory prerequisites for a smooth installation.
Hardware Requirements
These requirements suffice for deployment with 300 agents or less.
|
Item |
For 300 Agents |
For More Than 300 Agents |
With Reporting |
|---|---|---|---|
|
CPU |
2 vCPU |
4 vCPU |
Add 4 vCPU to the Existing System for Reporting |
|
Memory |
4 GB |
8 GB |
Add 4GB RAM to the existing System for Reporting |
|
Disk Space |
50 GB |
200 GB |
Add 250 GB Hard-disk for Reporting |
The gadget can be co-hosted with other Expertflow or third-party products.
Software Requirements
|
Item |
Recommended |
Notes |
|---|---|---|
|
Operating System |
Windows Server 2012 Standard Edition (x64) |
supported on this operating system |
|
JDK |
JRE 1.8 or higher |
Tested with JRE 1.8 |
|
Tomcat |
Tomcat 8.0,8.5 Not the Higher Version |
Tested with Tomcat 8.5 |
|
Browser |
Tested on latest Firefox |
|
|
Domain Signed Certificate |
|
Of Machine |
|
MS SQL SERVER |
SQL Server Version 2016 |
SQL SERVER would only be required if reporting is included, for reporting HA, the Customer needs to provide the SQL Cluster |
Reporting is Optional, If customer required reporting SQL Server would be requiredIf customer want High Availability for reporting,SQL Cluster would be required
Port Utilization Requirements
Whisper gadget rest API is deployed in tomcat. Any available port can be assigned to the service. The default HTTP port is 8080 and the HTTPS port is 8443. Local & network security policy should allow communication on the configured port.
System Access Requirements
-
Tomcat admin access
-
Windows machine Users with Admin rights
-
Cisco Finesse Administration access
-
Finesse Administration credentials.
-
Cisco Finesse agent desktop/supervisor desktop access
-
Finesse agent\supervisor users configured properly as per guidelines
Finesse Agent/Supervisor Configuration
-
The agent should have a hard phone.
-
Enable Built-In Bridge on both Extensions.
-
Monitoring Search Space enables both.
-
Disable G.722 codec from Agent and Supervisor Extensions
Application User Detail
One application/RMCM user required with the following property.
-
Permission and roles should be:
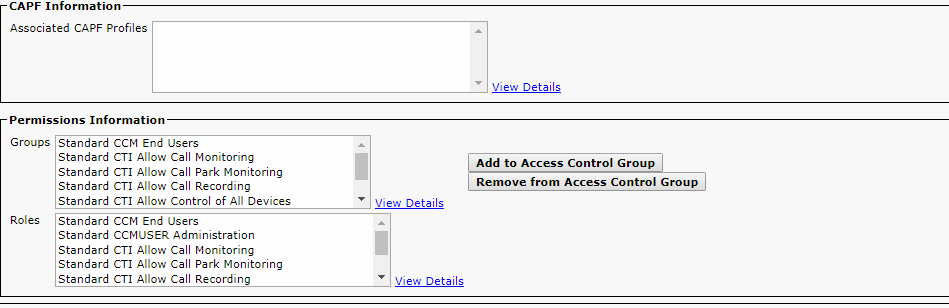
Ensure that only below Roles are added against the Application User:
-
Standard CTI Allow Call Monitoring
-
Standard CCM End Users
-
Standard CTI Allow Call Park Monitoring
-
Standard CTI Allow Control of All Devices
-
Standard CTI Call Recording
-
Standard CTI Allow Control of Phones supporting Connected Xfer and conf
-
Standard CTI Allow Control of Phones supporting Rollover Mode
-
Standard CTI Enabled
-
Supervisor devices part controlled Devices:
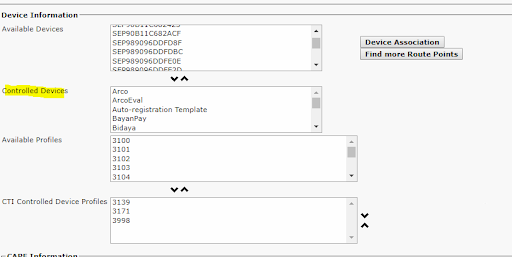
-
Credential configuration of user should be:
Time Synchronization Requirements
If the system date and time are not synchronized the system can produce unpredictable results. Therefore, please make every effort to adhere to the following time synchronization guidelines:
The server machine and Cisco Finesse should have their Time Zone and time configured properly according to the geographic region and synchronized. To configure the time zone, please see the instructions from the hardware or software manufacturer of NTP server. The application servers should be synchronized to the second. This synchronization should be maintained continuously and validated on a regular basis. For security reasons, Network Time Protocol (NTP) V 4.1+ is recommended.
Compatibility
|
Item |
Recommended versions |
Notes |
|---|---|---|
|
UCCE |
11.0 |
Tested on version 11.0 |
|
UCCX |
11.0 |
Tested on version 11.0 |
|
CUCM |
11.0 |
Tested on version 11.0 |
Browser Compatibility
|
Item |
Recommended versions |
Notes |
|---|---|---|
|
Firefox |
Recent versions |
Tested |
|
Chrome |
Recent versions |
Tested |
|
Internet Explorer |
Recent versions |
Not tested |
Phones Compatibility
The Expertflow Supervisor Whisper Gadget uses the BiB (Built-in Bridge) feature of Cisco phones. Any Cisco Hard phone that supports BiB should work. See here a list of those that do. Formal testing and QA is executed however only with phones listed in the tables below.
|
Item |
Tested Versions |
|
Hard Phone(s) |
CP-7965G |
|
Cisco Jabber Supported Version |
jabber Version 12.6.2.38119 Build 288119 |
Officially Cisco supports the Whisper feature only with Hardphone, IP Phone bug is mention here, However, we found during testing that this feature works with a certain version of Jabber. But there are limitations and technical constraints due to limited support at Cisco end
Configure Tomcat Service for SSL (Skip if you want to run on HTTP)
To install and configure SSL/TLS support on Tomcat, follow these simple steps:
1. Open the windows Command Prompt as administrator.
2. Navigate to JAVA_Installation/bin directory as shown below:
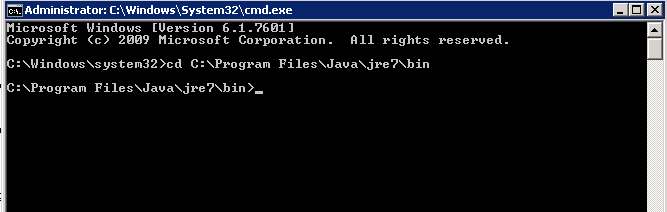
3. Create a keystore file to store the server's private key and self-signed certificate by executing the following command in windows terminal:
keytool -genkey -alias tomcat -keyalg RSA
After executing this command system will prompt you to answer the following questions:
Enter keystore password: password (choose any 6 digit password. Default is changeit)
Re-enter new password: password
What is your first and last name?
[Unknown]: XXXXX e.g Nabeel
What is the name of your organizational unit?
[Unknown]: XXXXX e.g. Call Center
What is the name of your organization?
[Unknown]: XXXXX e.g, Expertflow
What is the name of your City or Locality?
[Unknown]: XXXXX e.g Bern
What is the name of your State or Province?
[Unknown]: switzerland
What is the two-letter country code for this unit?
[Unknown]: XXXXX e.g. CH
Is CN=Nabeel,OU=Call Center, O=Expertflow, L=Bern, ST=switzerland, C=ch correct?
[no]: yes
Enter key password for
(RETURN if same as keystore password): changeit
Re-enter new password: password
This command will create a new file, in the home directory (e.g. in this case “C:\Program Files\Java\bin” ) of the user under which you run it, named ".keystore". To specify a different location or filename, add the -keystore parameter, followed by the complete pathname to your keystore file, to the keytool command shown above.
keytool -genkey -alias tomcat -keyalg RSA -keystore \path\to\my\keystore
-
UPdate the "SSL HTTP/1.1 Connector" entry in Tomcat_Home/conf/server.xml and modify as describe. Default configuration will look as show below:
<!--
<Connector port="8443" protocol="HTTP/1.1" SSLEnabled="true"
maxThreads="150" scheme="https" secure="true"
clientAuth="false" sslProtocol="TLS"
/>
Un-comment it and modify it to look like the following:
<Connector SSLEnabled="true" acceptCount="100" clientAuth="false"
disableUploadTimeout="true" enableLookups="false" maxThreads="25"
port="8443" keystoreFile="/Users/Zain/.keystore" keystorePass="password"
protocol="org.apache.coyote.http11.Http11NioProtocol" scheme="https"
secure="true" sslProtocol="TLS" />
If everything was successful, you now have a keystore file with a Certificate that can be used by your server. Start tomcat service and try to access https://localhost:8443 & http://localhost:8080 Urls in browser, You should be able to see the tomcat’s local home page.
Deployment
Web Service Deployment
1. Download the latest copy of the whisper coaching rest WhisperCoaching .war file from here, put the whisper coaching web service .war file inside the tomcat’s webapps directory.
2. Navigate to Apache-tomcat-home\webapps\WhisperCoaching\WEB-INF\classes directory and copy the jtapi.ini file and past that file to Apache-tomcat-home directory and then restart the tomcat server.
3. Navigate to Apache-tomcat-home\webapps\WhisperCoaching\WEB-INF\classes directory and update the following entries in config.properties file according to UCCE/UCCX deployment.
4. Add license key (If you don't have contact Expertflow )
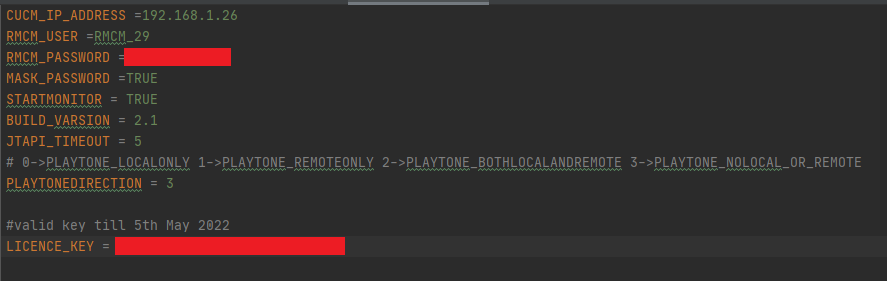
|
Variable |
Value |
Description |
|---|---|---|
|
CUCM_IP_ADDRESS |
192.168.1.26 |
agent and supervisors cucm ip address |
|
RMCM_USER |
RMCM_29 |
RMCM user used to connect jtapi with cucm |
|
RMCM_PASSWORD |
----------- |
RMCM password |
|
MASK_PASSWORD |
TRUE |
If true not printing the password in gadget logs |
|
STARTMONITOR |
TRUE |
If false used update monitor else used start monitor |
|
BUILD_VERSION |
2.1 |
print build version in logs |
|
JTAPI_TIMROUT |
5 |
max time for a request to wait for terminal connection and coaching to start, after that the request will be sent back with a failed response |
|
PLAYTONEDIRECTION |
3 |
use to determine to play tone on start of whisper coaching on not etc. |
|
LICENCE_KEY |
------------- |
Expertflow gadget license key |
If you enable StartMonitoring from the config then during start coaching two calls will be displayed on the agent desktop one call is from an agent to a customer call and the other is an agent to supervisor call for silent whispering. Once you end the coaching you have to restart the monitoring if you want to do silent monitoring.
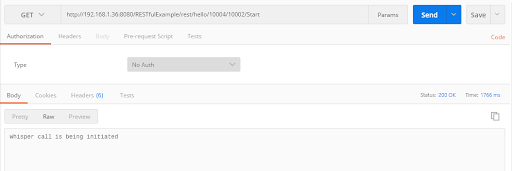
5. You can check the Web service accessibility from browser or postman app with the appropriate agent and supervisor’s extension you wish to coach and “Start” respectively. For example,
https://192.168.1.36:8443/WhisperCoaching/rest/whisper/43002/43004/Start
Where 43002, is the agent extension
43004, is the supervisor extension
The start is the coaching status switch. This informs the web service to create a whisper monitoring session.
5. Repeat the same steps for deploying the web service on the secondary server if you want to deploy the gadget in High Availability mode.
Finesse Gadget Deployment
Gadgets can be installed on your own web server or directly on the Finesse server. In order to install on the Finesse server follow these steps:
1. Down the latest gadget’s specifications files from here and extract files on the desired directory.
2. Open the Whisper.js file and update the web service Urls as per your deployment. If you are not deploying gadget in High Availability mode keep both Urls the same.

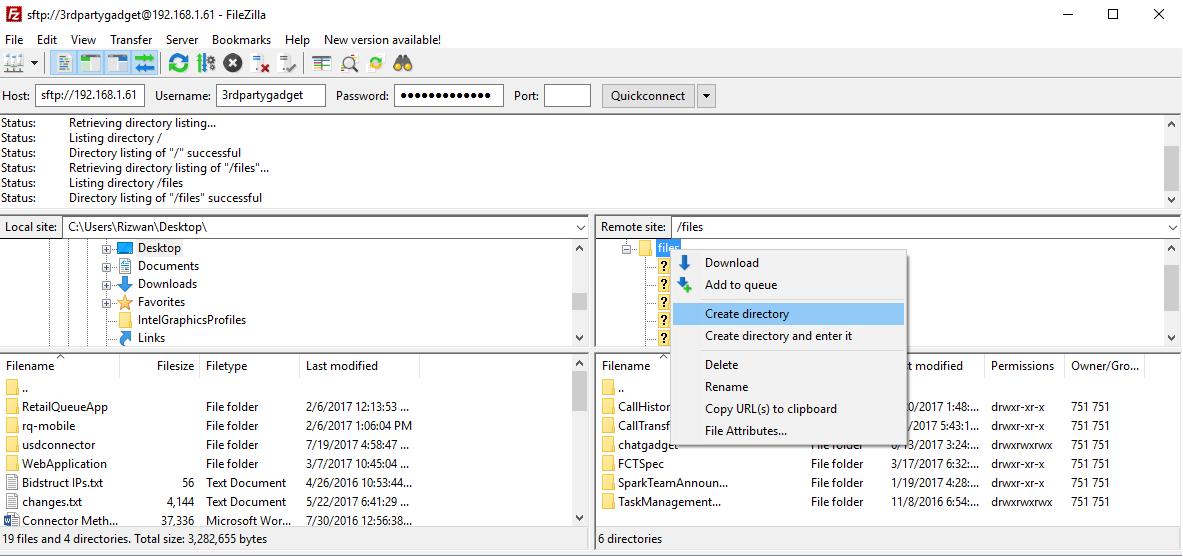
3. Run FileZilla and login to finesse using following credentials
4. Create a folder e.g. WhisperGadget into the files directory on finesse server and upload the specifications files and finesse server.
5. Repeat the same steps for deploying the gadget on secondary finesse server.
Finesse Gadget Layout Configuration
Next, we will update the Finesse layout to point to the new gadget. Load the Finesse administration by going to: https://<hostname or ip>:8445/cfadmin/
-
If your teams are utilizing the default layout, Click on the desktop layout tab. Otherwise, click on the Team Resources tab to edit a specific team's layout.
-
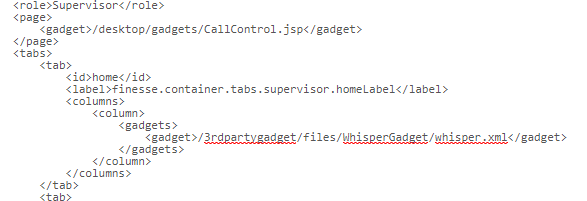
Where you place the Gadget is your preference. In this example I am placing the gadget under the HOME tab in a column under the supervisor role as shown below:
Adding SSL Exception in Browser
To avoid this add domain signed certificate.
This step should be repeated on all users (i.e. supervisor) machines where gadget is loading for the first time. Open the following URL in the browser and add the ssl certificate exception manually.