We will need to setup Vault before starting the application for database password encryption. We will use a single database user for all components of the application. If Vault is already setup up and running on some other server then we will just need to update two variables in a file in the next step. Follow the following steps to set up Vault locally.
-
Run these commands inside /root/supervisor-tools-deployment directory
# chmod 777 initVault.sh # ./initVault.sh -
Open this URL in browser http://supervisor-tools-ip/:8200/ui/vault/init
-
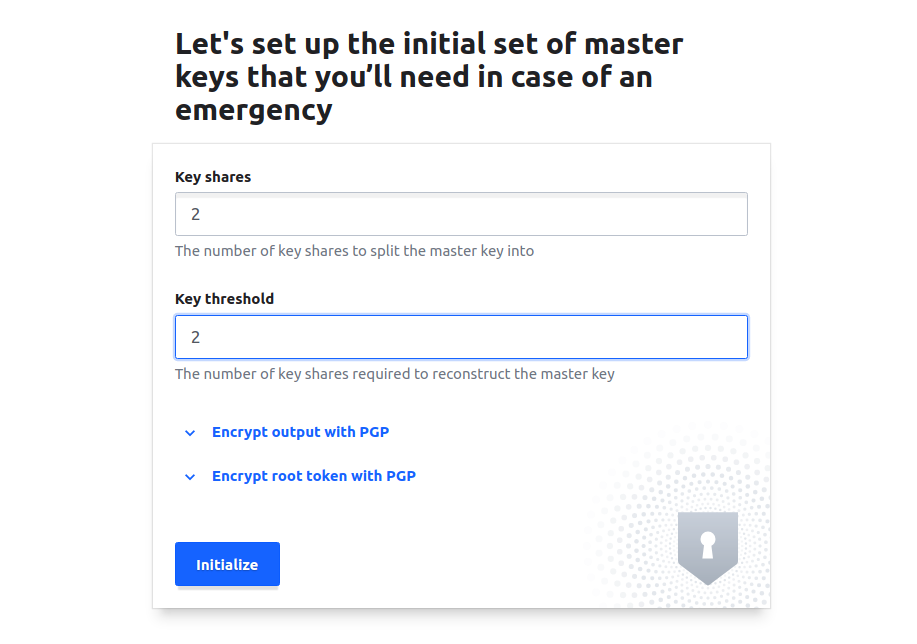
A form will open, enter 2 in both fields and click on Initialize button
-
The Initialize button will create a token and two keys. Token will be used for authentication and the two keys for unsealing the Vault. Click on the eye icon and copy these three values, save them and click on Proceed to Unseal button.
-
On the next screen, enter the first key in form and click on the Unseal button, enter the second key on the next page and click on the Unseal button.
-
Now enter the token and click on Sign in button. Vault is now configured and we can create secrets. A default Cubbyhole secret engine is created and we will use this engine to create a secret for the database password
-
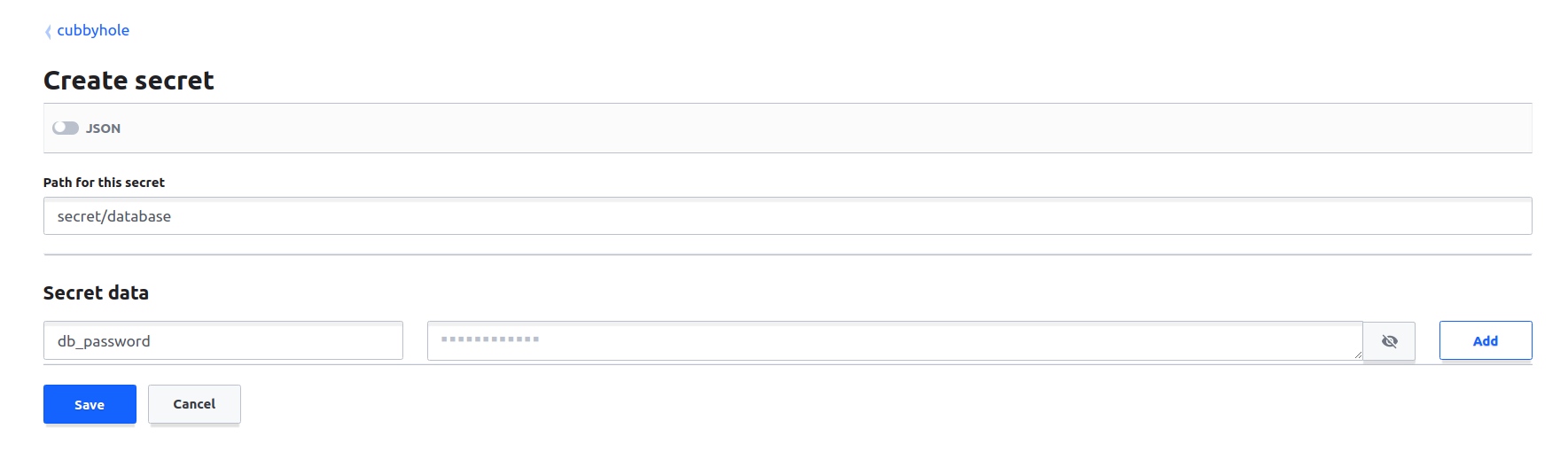
Click on the cubbyhole engine under secrets and then click on the Create secret button.
-
In create the secret form, enter secret/database in the path and under secret data, enter db_password in name and database password as its value, create on Add and then on Save button. A secret for database password in created now.
-
Notes: The path should be secret/database and secret name should be db_password. Vault should be unsealed if components need a restart or any of the components is restarted. Vault should remain unsealed as long as all components are not started.