This document provides comprehensive guidelines for configuring OAuth2 token lifespans in EF IAM according to industry security standards and best practices. The configuration follows recommendations from RFC 6749, OWASP security guidelines, and modern cybersecurity frameworks.
Industry Standard Token Lifespans
Based on security research and industry best practices, the following token lifespans are recommended:
|
Token Type |
Standard Lifespan |
Security Level |
Use Case |
|---|---|---|---|
|
Access Token |
15 minutes |
High Security |
API access, resource requests |
|
Refresh Token |
7 days |
Balanced |
Session persistence |
Security Rationale
-
Short Access Tokens (15 minutes): Minimizes the impact of token theft or interception
-
Medium Refresh Tokens (7 days): Balances security with user experience
-
Activity-Based Extension: Sessions extend with user activity, expire with inactivity
Configuration Settings
Realm-Level Configuration
We are going to implement following setting for Access and Refresh token lifespan as per RFC 6749, RFC 6750
Access Token Settings
Access Token Lifespan: 15m (900 seconds)
Access Token Lifespan for Implicit Flow: 15m (900 seconds)
Client Login Timeout: 30m (1800 seconds)
Login Timeout: 30m (1800 seconds)
Session Settings (Controls Refresh Token Lifespan)
SSO Session Idle Timeout: 7d (604800 seconds)
SSO Session Max Lifespan: 7d (604800 seconds)
Client Session Idle Timeout: 7d (604800 seconds)
Client Session Max Lifespan: 7d (604800 seconds)
Client-Level Configuration
Access Token Lifespan: 15m
IAM Admin Console Configuration:
-
First check the lifespan of your access and refresh token. This is the Postman API call to generate admin token, you can see that it has lifespan for both tokens is 30 minutes.
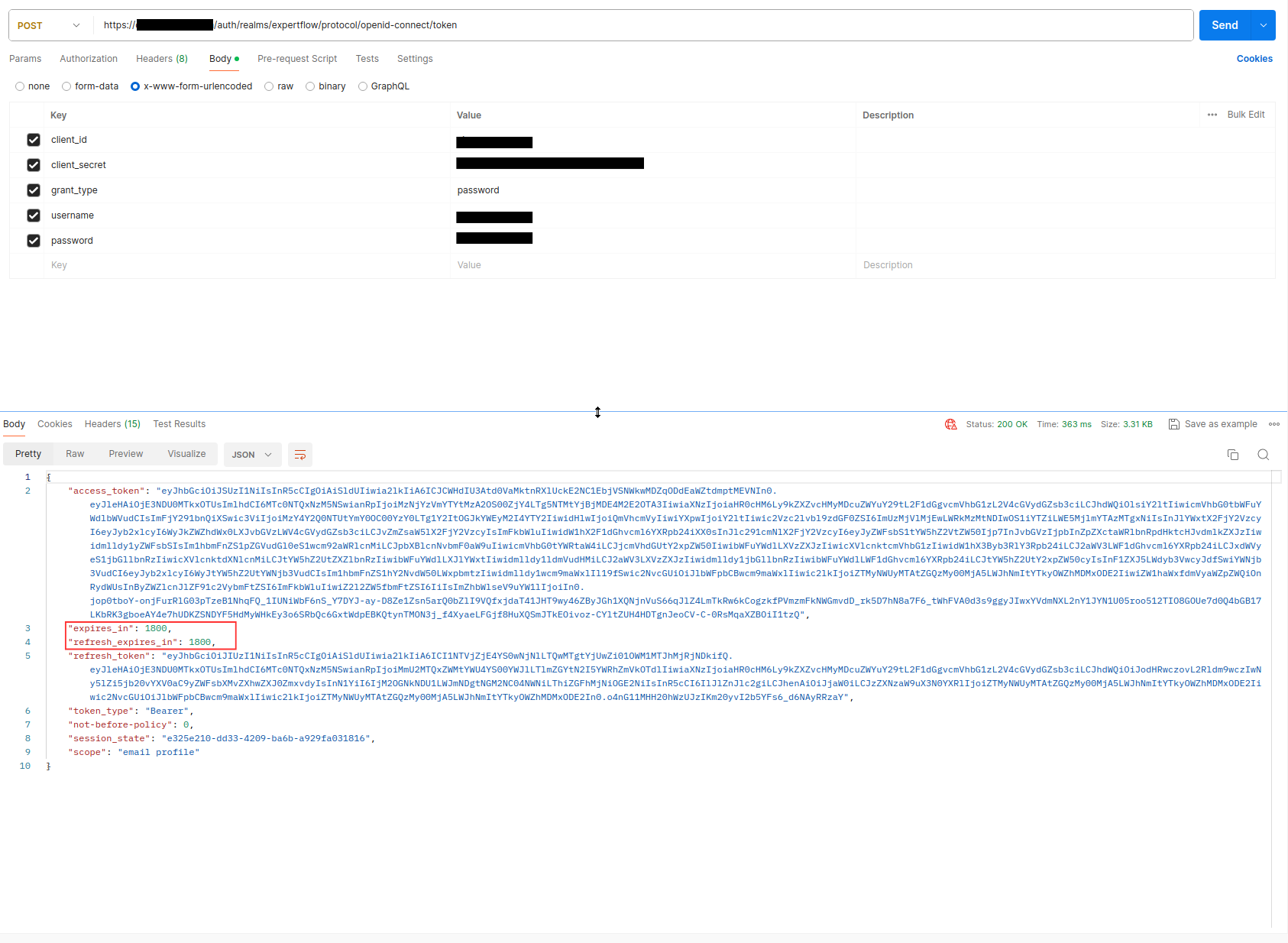
-
Now, go to your targeted realm in EF IAM and then click on Realm Settings under Configure tab (in this example its Expertflow).
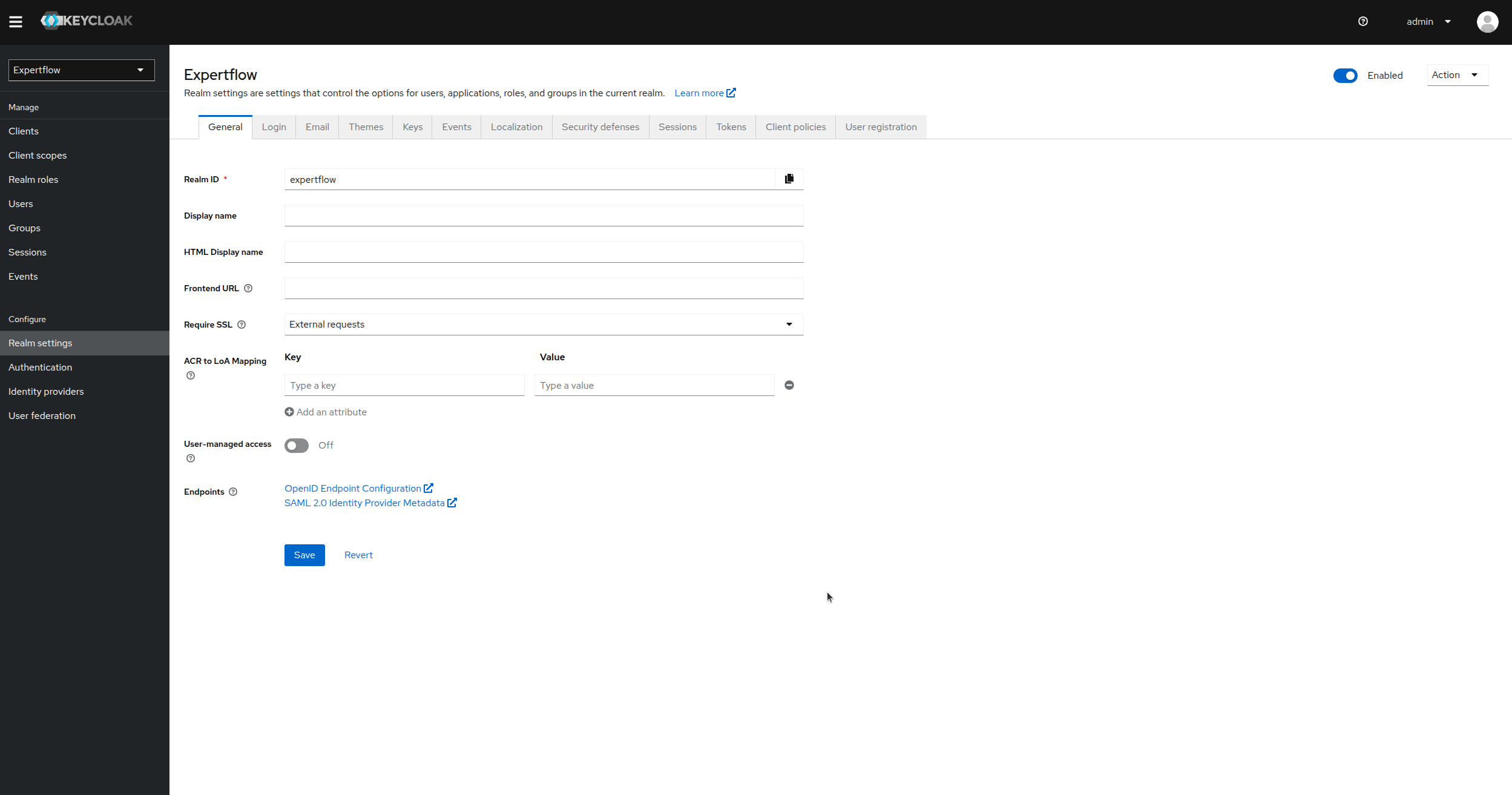
-
Click on Tokens tab in Realm Settings. Change all the setting as per configurations given below:
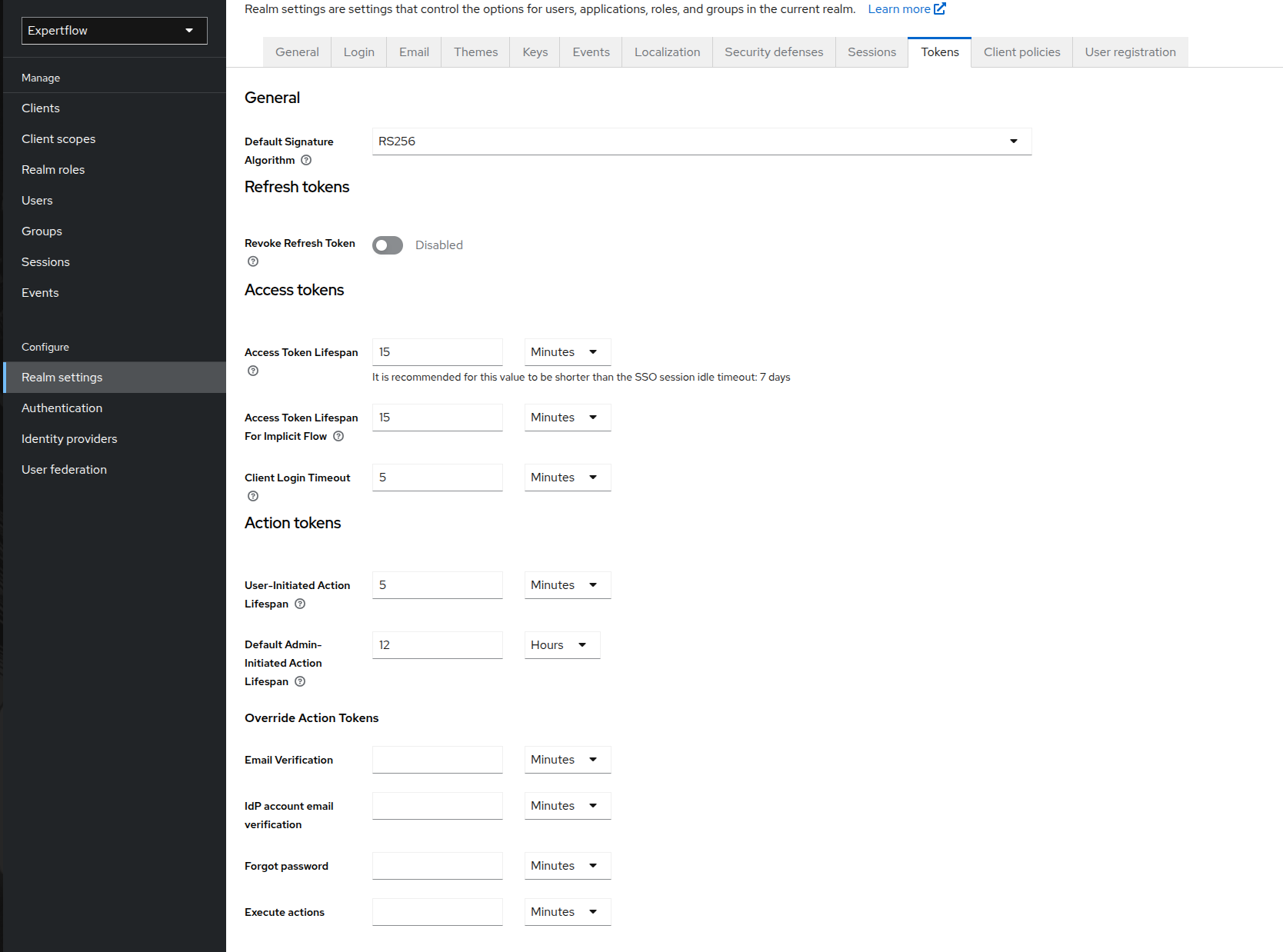
Access token session lifespan setting -
Click on Session tab in Realm Settings. Change all the setting as per configurations given below:
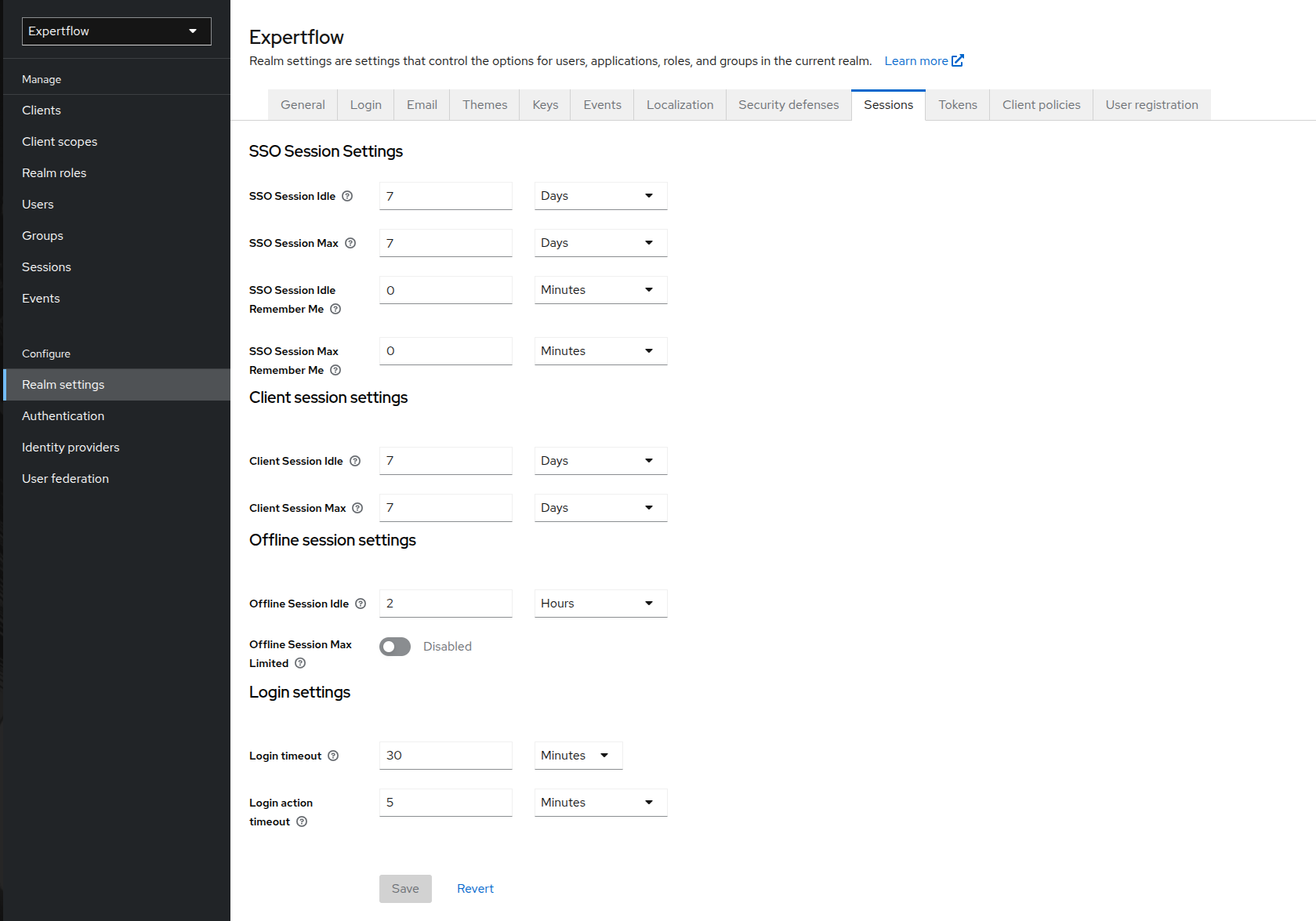
Refresh token session lifespan settings -
Now, click on Clients tab under Manage setting on left panel, then click on cim.
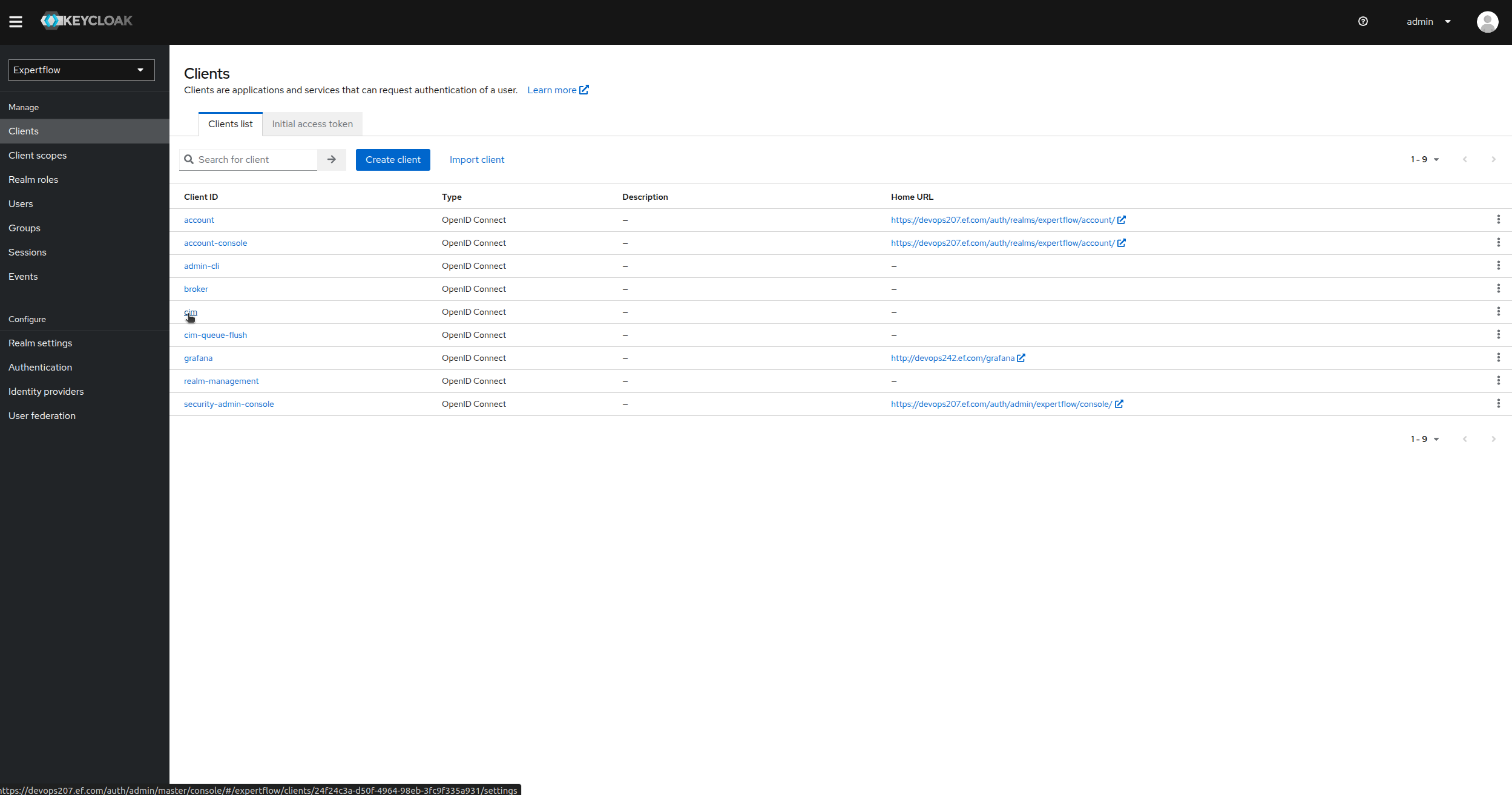
-
Click on Advanced tab in cim settings
-
Scroll down until you see Advanced Settings. Under which we can see Access token lifespan setting. This setting modifies the lifespan of our access token. Modify it as per configuration given below:
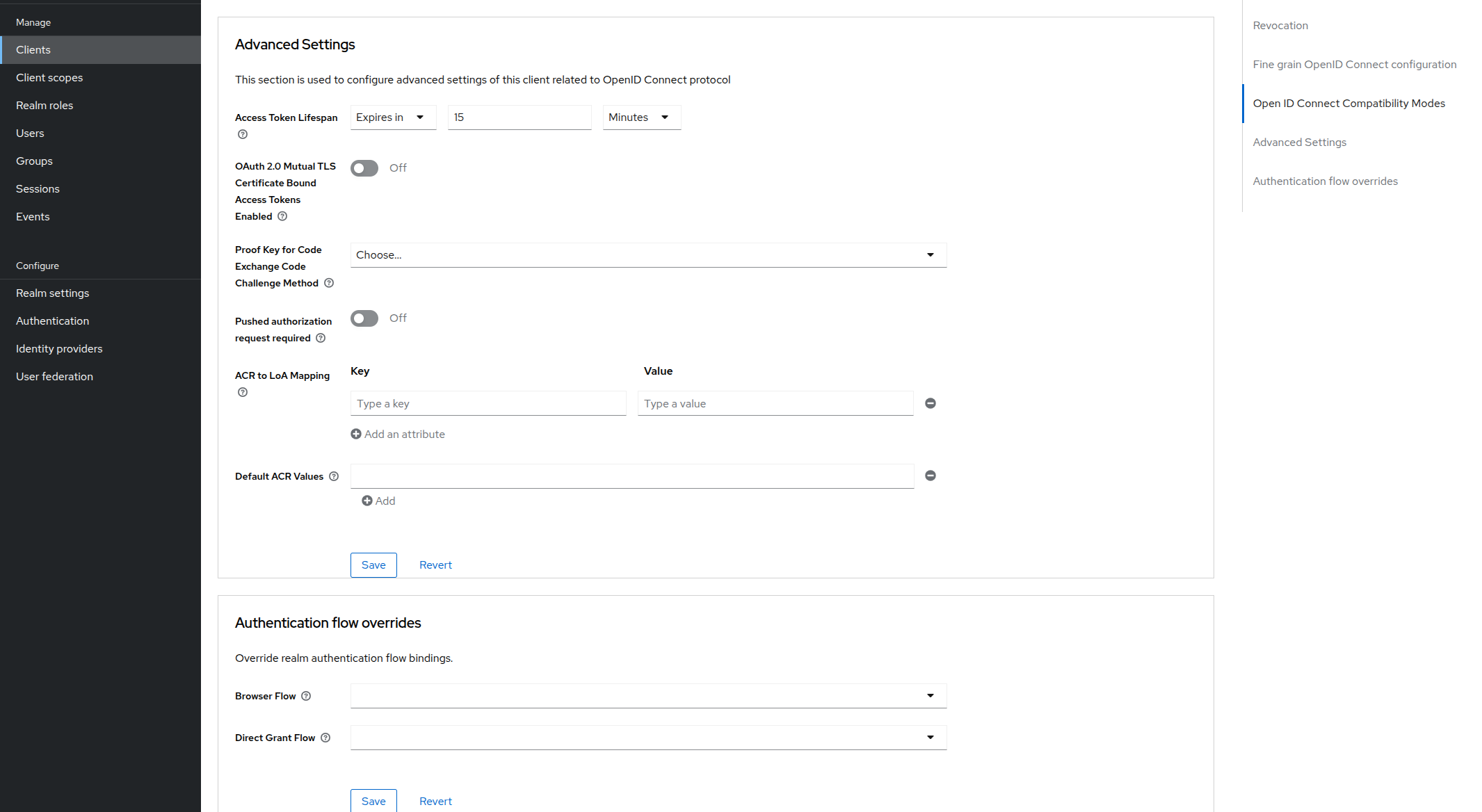
Access token lifespan as per client
Verification and Testing
Verify Token Configuration
-
Test Token Endpoint Response
curl -X POST \
http://localhost:8080/realms/{realm-name}/protocol/openid-connect/token \
-H 'Content-Type: application/x-www-form-urlencoded' \
-d 'grant_type=password&client_id={client-id}&username={username}&password={password}'
-
Expected Response Format
{
"access_token": "eyJhbGciOiJSUzI1NiIs...",
"expires_in": 900,
"refresh_expires_in": 604800,
"refresh_token": "eyJhbGciOiJIUzI1NiIs...",
"token_type": "Bearer",
"not-before-policy": 0,
"session_state": "a1b2c3d4-e5f6-7890-abcd-ef1234567890",
"scope": "profile email"
}
-
Key Verification Points
-
expires_in: Should be 900 (15 minutes) -
refresh_expires_in: Should be 604800 (7 days)
-
Token Refresh Flow Testing
# Use refresh token to get new access token
curl -X POST \
http://localhost:8080/realms/{realm-name}/protocol/openid-connect/token \
-H 'Content-Type: application/x-www-form-urlencoded' \
-d 'grant_type=refresh_token&client_id={client-id}&refresh_token={refresh-token}'
Detailed Setting Explanations
Access Token Settings
|
Setting |
Value |
Purpose |
Impact |
|---|---|---|---|
|
Access Token Lifespan |
15m (900s) |
Primary access token validity period |
Controls how often clients must refresh tokens |
|
Access Token Lifespan for Implicit Flow |
15m (900s) |
Token validity for SPA implicit flow |
Applies only to deprecated implicit flow |
|
Client Login Timeout |
30m (1800s) |
Authentication session duration |
Time allowed to complete login process |
|
Login Timeout |
30m (1800s) |
Maximum login flow duration |
Prevents abandoned login sessions |
Session Settings (Refresh Token Control)
|
Setting |
Value |
Purpose |
Impact |
|---|---|---|---|
|
SSO Session Idle Timeout |
7d (604800s) |
Inactivity timeout for user sessions |
Primary refresh token lifespan control |
|
SSO Session Max Lifespan |
7d (604800s) |
Absolute maximum session duration |
Hard limit regardless of activity |
|
Client Session Idle Timeout |
7d (604800s) |
Client-specific inactivity timeout |
Overrides realm setting per client |
|
Client Session Max Lifespan |
7d (604800s) |
Client-specific maximum duration |
Overrides realm setting per client |
Compliance and Standards
Industry Standards Compliance
|
Standard |
Reference |
Compliance Notes |
|---|---|---|
|
RFC 6749 |
Core OAuth2 implementation |
|
|
RFC 6750 |
Access token handling |
|
|
OWASP |
Security best practices |
|
|
NIST |
Identity assurance levels |